
Hacked
Financial information security in the digital age
By Kevin Manne
Jill Johnson, BS/MBA '02, was on vacation in Puerto Rico in 2009 when she received an email alerting her to suspicious activity on her credit card account.
"At first I thought it was just spam," says Johnson. "But I called the number on the back of my card and they told me they had denied two transactions for $600 at a Wal-Mart in Punta Gorda, Florida.
"I freaked out because I didn't know what to expect. I was really surprised and asked, 'How is this possible?' because I still had the card."
For Johnson, a CPA, FHFMA and audit principal at Lumsden & McCormick, credit card fraud has become all too familiar. Since that first experience in Florida, she's had five other cards compromised, and not all from the same bank.

"I freaked out because I didn't know what to expect. I was really surprised and asked, 'How is this possible?' because I still had the card."
Jill Johnson, BS/MBA '02
CPA, FHFMA, Audit Principal at Lumsden & McCormick
It's a situation that millions of credit card users have found themselves in: Someone, somewhere, has stolen their information and is amassing hundreds, even thousands of dollars worth of charges—and the card owner has no idea how it could've happened.
Victims may find bogus charges on their monthly statement, or they may receive an alert from their bank via text message, phone call or email. But no matter how they find out, victims feel confused, distrustful and even panicked.
Arun Jain, Samuel P. Capen Professor of Marketing Research in the School of Management, says he noticed something was wrong with his credit card bill when the monthly total was significantly higher than usual.
"We didn't usually check the individual items on the statement, which is very bad," says Jain. "But I started looking closely and found that while we were in India, there were charges in the U.S. at places that we never go to. That's what set off alarms for me, and I called the credit card company to get it straightened out."
Both Jain and Johnson say while the credit card companies removed any fraudulent charges from their bills, they have become more cautious with their accounts. They also agree that more secure systems are needed to protect consumers.
A rising threat
When the credit card data of some 70 million Target shoppers was compromised during the 2013 holiday season, it wasn't the first time consumer confidence in data security was shaken—and it wouldn't be the last. Less than a year later, the nation's largest home improvement retailer, Home Depot, announced that its payment data systems also had been breached.
In all, more than 500 million financial records were hacked in the 12 months between October 2013 and 2014.

"We didn't usually check the individual items on the statement, which is very bad. But I started looking closely and found that while we were in India, there were charges in the U.S. at places that we never go to. That's what set off alarms for me, and I called the credit card company to get it straightened out."
Arun Jain
Samuel P. Capen Professor of Marketing Research
At a cybersecurity event organized by the Financial Services Roundtable last year, FBI and Secret Service officials told business leaders that the U.S. financial sector is one of the most targeted in the world.
Globally, card fraud losses have risen from just over $2 billion in 2000 to more than $11 billion in 2010, according to the 2013 Nilson Report.
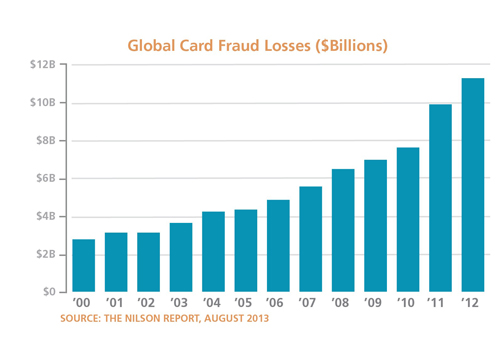
It's all part of a modern wave of cybercrime that allows thieves to pull off a bank heist from the comfort of their own homes. But even as crooks become more sophisticated, new technology and systems are here and on the horizon to help protect your personal and financial information.
Why cybercrime?
Experts say payment card data is attractive to criminals because it's an easy target with low risk and a high, convenient payout. Payment cards include credit cards, debit cards and stored value cards—any card that features a Visa, MasterCard, Discover or American Express logo.
"Think of a cyberthief just like any other business entrepreneur," says Tim Mongan '82, a banking industry data security project consultant in Raleigh, North Carolina. "They're trying to get the most benefit they can with as little risk as possible and today that generally equals payment card theft."

"[Cyberthieves are] trying to get the most benefit they can with as little risk as possible and today that generally equals payment card theft."
Tim Mongan '82
Banking Industry Data Security Project Consultant
Once they have the information they need, thieves can then almost immediately start turning their crime into benefits via Internet purchases. Online, a merchant doesn't know anything about the buyer other than the data they're required to enter to make a purchase, making the thieves faceless and easing their ability to cash in.
There are restrictions and built-in protections to using stolen information for purchases online, however. Lewis Mandell, professor emeritus of finance and managerial economics, says stolen account information can only safely be used online a few times.
"First off, how are online crooks going to get the things they order?" Mandell asks. "They're not going to have packages shipped to their house because it points the cops right to your home. You can maybe open a post office box but you can only do that one or two times and pretty soon they discover that it's a stolen item."
Mandell says merchants like Amazon will give priority shipping to loyal customers, but can delay shipping on newly created accounts, giving the retailer time to check if the payment card information has been reported lost or stolen before shipping.
Another big reason cybercrimes are attractive is that the criminals are unlikely to get caught or face prosecution, according to Mongan.
"There are tremendous problems in tracking down the thieves when there's a heist," he says. "Geographically, they can be located hundreds of miles from the online merchant's location or even thousands of miles away in other countries, which creates problems with legal jurisdiction even if you do find out who it is and where they are."
A high-tech security shift
In the United States, the technology for point-of-sale purchases has remained virtually unchanged for more than half a century-largely due to the daunting infrastructure upgrades required to make a system-wide change.
Protected plastic
A coordinated effort is underway to roll out a new system of payment cards that will combat fraudulent in-store purchases. Known as chip and PIN cards, these cards contain a microchip and may also require consumers to enter a personal identification number (PIN) rather than provide a signature when making a purchase at terminals that support chip cards.
The microchip makes the process of duplicating physical cards much more difficult and the PIN helps stop thieves in their tracks.
"A card with a PIN is more secure simply because the person who steals your wallet and has your credit card probably doesn't know what your PIN is," says Mandell. "That gives you a higher level of security, provided people aren't stupid enough to write their PINs down on their card or carry a list of PINs in their wallet."

"A card with a PIN is more secure simply because the person who steals your wallet and has your credit card probably doesn't know what your PIN is. That gives you a higher level of security, provided people aren't stupid enough to write their PINs down on their card or carry a list of PINs in their wallet."
Lewis Mandell
Professor Emeritus of Finance and Managerial Economics
Card issuers and merchants are busy preparing for the transition to process these new cards in the United States. While similar systems have been in place in Europe and other parts of the world for years, experts say it could take as long as three to five years to make the switch in the U.S. due to the high level of complexity in card data processing here.
However, some retailers have gotten an early jump on installing the readers needed for chip-embedded cards in their stores. At a Senate hearing in February 2014, Target reported that it had already installed the readers in 300 of its stores and planned to have them in place at all of its stores by the end of the year.
Mobile money
Another innovation that looks to make in-store credit card purchases more secure is payment via mobile devices, especially when paired with biometric identification. With the Apple Pay system on Apple's iPhone 6 and iPhone 6 Plus, the biometric identification is your thumbprint. Without a match on the device's built-in Touch ID system, a payment will not be authorized.
As an additional layer of security, once the thumbprint is matched and the payment is approved on the iPhone, the card transaction data is translated into an alias code that can be used only once, a process known as tokenization.
This process keeps your credit card information out of merchant systems altogether. Had a tokenization system been used prior to the recent large data breaches at Target, Home Depot and others, there would have been no data for the thieves to use.
It's important to note that while chip and PIN cards improve security at in-store purchases, they do not make online transactions more secure since the card is not physically processed. And, while an iPhone can be set to require a thumbprint to authorize purchases in the iTunes, iBooks and App stores, it will not help in online systems outside of the Apple ecosystem.
Staying safe
Though technology will improve data security, industry experts recommend consumers stay vigilant and take pre-emptive action to protect their accounts from fraud.
Mandell says a simple step is to carry as few credit cards as possible.

"Some people are really good—they'll monitor their credit card statements online every day or every week. At a minimum you should check your statements when they come in the mail."
Patricia Herberger '79, MBA '85, SPHR
President of Herberger Consulting Group and Independent Associate with LegalShield
"You walk into a department store and they will say 'Sign up for our store credit card and we'll give you 10 percent off your purchase,'" he says. "You do that and now you're exposing all of your information to possible catastrophic use. For the most part you can get by with a single Visa or MasterCard."
Patricia Herberger '79, MBA '85, SPHR, president of Herberger Consulting Group and independent associate with LegalShield, says credit card users should regularly check their statements, especially if they suspect their data is at risk.
"Some people are really good—they'll monitor their credit card statements online every day or every week," says Herberger. "At a minimum you should check your statements when they come in the mail."
For in-store purchases, Herberger says shoppers should also avoid allowing store personnel to handle their card out of sight whenever possible.
When shopping online, an easy way to tell if the transaction is secure is to look for "https" at the beginning of the address in the Web browser. The 's' indicates that the data is encrypted using Secure Sockets Layer - Transport Layer Security (SSL-TLS), which makes the information accessible only to the person-or computer-with the correct key to decode it.
Consumers also should use well-known, trusted websites and look for evidence that they meet Payment Card Industry Data Security Standards (PCI-DSS) and undergo frequent security vulnerability tests such as McAfee Secure.
Looking ahead
Today, the number of merchants who can process chip cards and mobile payments remains limited. The American Bankers Association estimates that only about half of banks and retailers will be transitioned to the microchip system by October 2015. In addition, a battle over transaction fees is preventing a single mobile payment standard from being adopted at all retailers.
"We have a lot to gain and little to lose by going to the cards with microchips," says Mongan. "The technology, though, is in its infancy in terms of adoption in the U.S. There is a lot of IT infrastructure that needs to be put in place."
In the end, Mandell says as long as the payoffs remain high and the risks remain low, don't look for payment card fraud to disappear any time soon.
"There are no foolproof security systems, and there are a lot of crooks out there because it's pretty easy money and their systems are very well developed to trade these credit card numbers," he says. "They go after the easy money. It's the old Willie Sutton thing: you rob banks because that's where the money is."
How card payments work
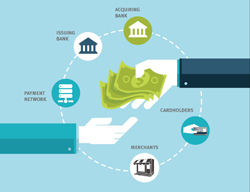
It's easy to ignore just how much happens behind the scenes when you swipe the magnetic stripe—also known as a magstripe—on the back of your card through a terminal to make a purchase.
The magnetic stripe typically contains three tracks of data. The first and second tracks hold the information from the card such as the customer's name, the account number, expiration date and country code. The third track can contain additional information if necessary, but generally goes unused on most cards and isn't even present on cards with a narrower magnetic stripe.
Once swiped, the system will check with the credit card company to ensure that the card has not been reported stolen and that it's under the credit limit.
A standard payment card transaction involves five parties:
- Payment brand networks, which process transactions to the correct credit card issuer so funds can be delivered from a customer's account to the merchant. They're responsible for the networks that connect all of the parties at the highest level, like VisaNet, Visa's global payment system.
- Issuing banks, where the consumer gets their card, lines of credit and bills.
- Acquiring banks, where the merchants get the ability to accept certain cards and route the transactions.
- Merchants, where a consumer purchases goods and services.
- Cardholders, who present payment cards to merchants to make purchases.
7 computer security tips you need to know (and actually follow)
Credit card data isn't the only information you should be mindful of. David Murray, associate professor of management science and systems, recommends these best practices to help secure your computer data and keep your online accounts safe:
- Use long passwords. Create a complex password that's easy to remember by using a passphrase. To do that, put a short, personally relevant sentence together to make one long string of characters—preferably with a number and special character somewhere in there too. Check how long it would take a desktop PC to crack your password at howsecureismypassword.net.
- Use different passwords. In a perfect computer security world, you'd have a different, long, complex password for each of your online accounts. Easier said than done, right? If you're not going to do it for every account, at least do it for sites that contain your personal and financial information.
- Back up your data. If your hard drive crashed today or your cell phone fell into a lake, how much information would you lose forever? Grab an external hard drive and set your computer to back up automatically to it each day. For extra security, keep a backup in a different location in case of fire or natural disaster.
- Passcode your cellphone. With access to your social networks, email, bank accounts and more, your cellphone is one nice convenient package of potential identity theft. Enable the passcode feature and turn on GPS location security like the Find my iPhone app on iOS or Device Manager on Android to help track down your lost or stolen smartphone.
- Be careful what you click. Always be mindful of the links you're clicking on, especially from emails and social networks. Messages that ask for usernames and passwords are red flags.
- Mind your app installs. Before you install apps on your computer or mobile device, take a look at user reviews to see if others have had problems with the software. Stick with apps from companies with good, established reputations you can trust.
- Exercise good digital hygiene. Keep the software up to date on all your digital devices and be sure to run an anti-virus program. Both will make it harder for hackers to compromise your system. Check if your software is vulnerable at browsercheck.qualys.com.
